what to do if victim of facebook phishing
Teach Someone to Phish and They Can Feed Themself Forever…
Or maybe, we work harder to avoid phishing.
Phishing is a class of social technology that attempts to steal sensitive information. An attacker's goal is to compromise systems to obtain usernames, passwords, and other account and/or financial information. They most frequently accomplish phishing attacks via email. The assaulter sends crafted emails to people within an organization. The email commonly pretends to be from someone trustworthy, like your bank, UPS/FedEx, a credit carte company or an airline, or some other site for which you may take login credentials. The electronic mail includes a link to an "official" website that is actually a false site operated by the attacker.
 Once the user visits the faux site, they may exist asked overtly to enter account information such as usernames, passwords, credit carte details, social security or bank account numbers. The victim may besides be exposed to malware by the fake site. Taking advantage of a variety of vulnerabilities in the browser, the attacker may be able to install a Trojan Horse on the user's computer. If done correctly, the attack tin capture sensitive information without the victim even knowing that they take been compromised.
Once the user visits the faux site, they may exist asked overtly to enter account information such as usernames, passwords, credit carte details, social security or bank account numbers. The victim may besides be exposed to malware by the fake site. Taking advantage of a variety of vulnerabilities in the browser, the attacker may be able to install a Trojan Horse on the user's computer. If done correctly, the attack tin capture sensitive information without the victim even knowing that they take been compromised.
Why Phishing Works
Such attacks are particularly troublesome when the victims are privileged users within an organization. Suppose a user has privileges to approve or send checks, or authorize a bank transfer such as an ACH transfer. If that user tin be tricked into giving upwardly their username and countersign, then an imposter can potentially re-utilise the official username/password to initiate their ain transfer. Since the transfer is being authorized by an appropriate account holder (equally far every bit the organisation is concerned, with a valid username and password) it is harder to place this equally fraud without additional monitoring and validations.
Attackers apply more advanced and more than determined phishing methods if they are sure they have identified high value account holders. "Spear phishing" includes techniques to ensure that the attacks are successful. An assailant might, for example, develop their target employee list, and and so check social media pages like Facebook for interests, children's names and schools, and other available information to gather detailed intelligence that they can utilize to craft a targeted electronic mail. You may not automatically reply to an electronic mail from your bank, but would an email from your dealer near an emergency recall find on your new car, or a notice from a pharmaceutical company about critical side furnishings of a prescription drug yous are taking, or an email about your girl's fiscal aid at college be likely to get some attention? These targeted emails are usually highly effective.
Current phishing attacks against fiscal institutions are very customized. They are designed to be effective in these environments by targeting large numbers of financial institution employees. The goal is to infect and compromise enough users that the assaulter tin can go end-to-end command of financial transaction approval systems, assuasive him to initiate and corroborate transactions that appear to be properly authorized. These attacks use tailored techniques, dynamic websites, and regularly update the methods used. The event is a series of attacks that take an alarmingly high success rate, still a relatively low detection rate.
As far equally we know right now, these attacks take mostly been conducted confronting small-to-medium sized banks and credit unions, but some big banks and other financial organizations have been specifically targeted. The resulting compromises accept allowed fraudulent wire transfers of sizeable amounts - $400,000 to 900,000, and sometimes more. Attackers are oft able to browse an arrangement's accounts and specifically select accounts with the highest balances.
Avoid Becoming a Victim
Organizationally, in that location are things yous can do to aid avert becoming a victim, and to minimize damage if you are victimized:
1. Consider using dedicated systems for payment requests and approval processes. Consider disabling email admission on any organization involved with payment processing. If an assaulter cannot compromise the systems in payment processing, he will take a harder time obtaining payment usernames and passwords, and a harder fourth dimension actually requesting/blessing a transfer.
two. Consider using a strong authentication mechanism on all payment processing systems. This would include replacing or augmenting username/password combinations with a hardware token and Pin, or with biometrics such equally a fingerprint reader. An attacker will be unable to copy and reuse strong authentication such equally a token or biometrics.
iii. Consider blocking Internet access for systems involved in payment processing. If the system genuinely has no Internet admission, malware would exist unable to talk back to its controlling systems and attacker.
iv. Consider disabling the apply of USB flash drives in payment processing systems. In some circles USB flash drives are often referred to as "malware delivery devices." Disabling USB wink drives removes one more potential avenue for infection.
5. Use tools available in your email client. Outlook, for case, has the ability to help filter potentially harmful links. In Outlook, become to Tools/Options/Preferences/Junk Email/Options, and check "Disable links and other functionality in phishing messages" and "Warn me about suspicious domain names in eastward-mail addresses." These are not perfect solutions simply they can assist.
6. Be diligent in your utilize of anti-virus and anti-malware software, including regular updates and scans. Most of the malware used as office of a phishing assail is not detected by standard anti-virus software, simply some of it is. Some malware indicators may not exist changed before an anti-virus update is available, and sometimes older versions of malware are distributed. Additionally, anti-virus software can assistance identify secondary infections that may exist related to an attack.
7. Use reputation-based website, IP accost, and URL filtering to help ensure that whatever systems accessed from within the company are not considered "bad" sites. You lot can extend this further by allowing only "white-list" access – access to addresses that accept specifically been recognized as "skillful" sites (note that this has the potential to inhibit some Internet capability).
viii. Consider enforcing time-of-day login and payment processing. Many fraudulent transactions occur after normal working hours. For instance, a series of big transfers that completed at vii:00PM Friday evening might exist functionally ignored until staff render and see aberrant activities Monday morn.
9. Consider limiting access to payment processing systems from mobile devices, laptops, and systems based in dwelling house offices. These distributed systems are typically more than vulnerable to threats.
10. Do not allow admission to any internal organization system, especially payment processing systems, from a personally endemic home estimator. There is just no style the organisation tin enforce proper control over such a system.
11. Deport employee security awareness sessions to instruct employees on how to identify phishing emails and avoid falling victim to them. Any reduction in exposure slows compromise and increases your organization's capability to identify an escalating threat.
12. Explicitly communicate to employees, partners and clients that you will never solicit business relationship information via email, or send a link to update account data.
Individually, there are things employees can do to help avoid condign a victim and compromising the integrity of organizational operations:
i. Never open attachments or links in unsolicited emails.
two. In general, be suspicious of all emails containing links. If you go an electronic mail with a link for yous to click, do not click it. Navigate independently to the destination site (for case, by typing www.mybigbank.com into a new browser window) and observe the referenced location without using the conveniently included link.
3. Do not respond to suspicious emails in any manner.
iv. Do not admission emails on the same computers used to initiate or approve payments.
5. Make management aware when you receive a suspicious email.
Examples of Phishing Emails
You can refer back to a previous column I wrote on here for a detailed breakdown of a phishing e-mail. But what if the email is not as breathy as the 1 I dissected before?
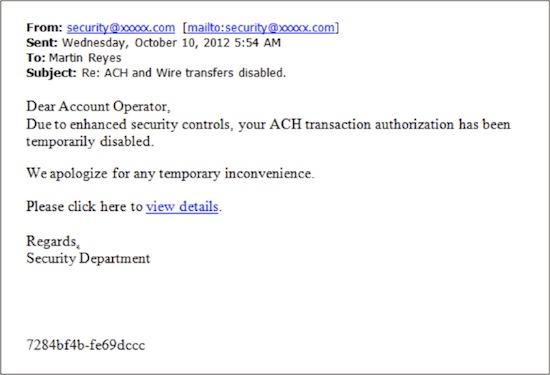
For purposes of this analysis, we volition presume that "Account Operator" is a reasonable role in your organization. The attacker has gathered plenty intelligence to know that the salutation is appropriate. Also presume that the arrangement name replaced with xxxxx.com is the name of your arrangement. What is wrong with this e-mail?
one. Effectively, not much. By all appearances this is an email that came from your own security department providing notice that your ACH privileges have been at to the lowest degree temporarily revoked.
two. Checking the email accost will show nothing as the email address has been spoofed.
three. Your start inkling should exist that the email has a generic salutation. If this e-mail actually came from your own security section, information technology would probably be addressed to "Martin", or "Mr. Reyes", and non to the task function.
four. The but existent clue in this electronic mail is the hyperlink available at "view details." In most browser-based email clients and some clients like Outlook, hovering over the hyperlink field will show the embedded link without actually opening it. The hyperlink pointed to a site that was completely unrelated to the system, something similar to this: "http://jkdev.nodonenet.com/forwarding.htm"
Chances are that you lot have been the target of a phishing assault. If you are in the fiscal community, chances are that yous accept been exposed to defended attacks – and will be again. Your best protection against phishing attacks is a combination of preparation and awareness that can limit the success of phishing attacks, and technical controls that will assist identify compromised systems and attempts past those systems to talk to hostile servers on the Cyberspace.
Source: https://www.securityweek.com/why-phishing-works-and-how-avoid-becoming-victim

0 Response to "what to do if victim of facebook phishing"
Postar um comentário